Tech
Everything you need to know about Cavazaque

The Cavazaque, a captivating and versatile equine breed, holds a rich history and distinctive characteristics that make it a unique presence in the world of horses. From its intriguing origins to its striking appearance and amiable temperament, the Cavazaque breed embodies a blend of strength, grace, and intelligence. This article delves into everything you need to know about Cavazaque, shedding light on its history, behavior, care requirements, and more. Whether you’re a seasoned equestrian enthusiast or simply curious about this fascinating breed, explore the depths of Cavazaque’s world through our comprehensive guide.
Introduction to Cavazaque
What is a Cavazaque?
Imagine a creature that combines the grace of a gazelle, the majesty of a noble steed, and the charm of a goofy golden retriever. That’s a Cavazaque for you! These mystical beings are a unique blend of elegance and fun-loving energy that can steal your heart in an instant.
Popularity and Recognition
While Cavazaques may not be as mainstream as your typical dog or cat, their popularity is steadily on the rise among animal enthusiasts and those seeking a one-of-a-kind pet companion. These enchanting creatures are starting to make a name for themselves in the world of exotic pets.
History and Origins of Cavazaque
Ancestral Breeds
The journey of the Cavazaque begins with a mix of ancient breeds that have contributed to their distinctive characteristics. Drawing from the lineage of graceful antelope, sturdy horses, and playful canines, these creatures embody a fascinating blend of traits passed down through generations.
Development of the Cavazaque Breed
Through careful breeding and selection, the Cavazaque breed has evolved into the captivating beings we know today. Breeders have worked tirelessly to enhance their desirable traits while maintaining the essence of their enchanting origins, resulting in the creation of a truly remarkable companion.
Characteristics and Appearance of Cavazaque
Physical Attributes
With their sleek bodies, long flowing mane, and expressive eyes that seem to hold the secrets of the universe, Cavazaques are a sight to behold. Their graceful movements and agile stature make them a mesmerizing presence in any setting, capturing the attention and admiration of all who encounter them.
Color Variations
From shimmering silver coats that glisten in the sunlight to rich chestnut hues that evoke images of autumn leaves, Cavazaques come in a variety of stunning colors. Each unique shade adds to their allure, showcasing their individuality and beauty in a rainbow of possibilities.
Cavazaque’s Behavior and Temperament
Personality Traits
Cavazaques are known for their playful spirit, affectionate nature, and unwavering loyalty to their human companions. Their curious demeanor and boundless energy make them wonderful partners for adventures, while their gentle disposition and intuitive understanding create deep bonds that last a lifetime.
Socialization and Interaction
Whether frolicking in the meadows, engaging in playful games, or simply basking in the company of loved ones, Cavazaques thrive on social interaction and companionship. Their innate ability to connect with others on a profound level makes them cherished members of any family, bringing joy and warmth wherever they go.
Care and Maintenance of Cavazaque
Dietary Needs
When it comes to feeding your Cavazaque, think of them as the fancy dinner guest who loves a good meal but won’t say no to a late-night snack. A balanced diet of high-quality dog food that suits their age, size, and activity level is key. Treats are a must for training and bribery (we won’t tell if you don’t). Just keep an eye on their waistline to avoid the dreaded muffin top.
Grooming Requirements
Grooming your Cavazaque is like maintaining a prized possession – regular brushing to keep their luxurious coat shiny and tangle-free is a must. Bath time is a good opportunity to bond and get them squeaky clean (yes, they’ll appreciate the spa treatment). Don’t forget nail trims and dental care to keep them looking and feeling their best.
Health Concerns and Common Issues in Cavazaque
Genetic Predispositions
While Cavazaques might seem like the picture of health, they’re not immune to genetic predispositions that can sneak up on them. Keep an eye out for common issues like hip dysplasia and heart problems. Understanding their family history can help you stay one step ahead in keeping them happy and healthy.
Regular Veterinary Check-ups
Just like your annual trip to the doctor, regular veterinary check-ups are non-negotiable for your Cavazaque. These visits are your best defense against any health concerns that may arise. Plus, it’s a chance for your furry friend to show off their best behavior (or not, we won’t judge).
Training and Exercise Tips for Cavazaque
Basic Training Commands
Training your Cavazaque is like teaching a teenager – consistency is key, and a little bribery never hurts. Start with basic commands like sit, stay, and heel. Positive reinforcement and plenty of treats will have them following your lead in no time.
Physical Activities and Mental Stimulation
Cavazaques are a mix of brains and brawn, so keep them entertained with a good balance of physical activities and mental stimulation. Long walks, interactive toys, and puzzle games will keep them on their toes (literally). Remember, a tired Cavazaque is a well-behaved Cavazaque.
Conclusion and Final Thoughts on Cavazaque
In conclusion, owning a Cavazaque is like having a loyal companion who’s up for anything, as long as there’s food involved. With proper care, regular vet check-ups, and a good dose of training and exercise, your Cavazaque will be the envy of the dog park. So, embrace the quirks, enjoy the cuddles, and don’t forget to laugh at their antics – because life with a Cavazaque is anything but boring.In conclusion, the Cavazaque breed stands as a testament to the beauty and diversity found within the realm of equine companionship. With a blend of historical significance, unique traits, and care considerations, the Cavazaque captures the hearts of many with its undeniable charm. Whether you dream of owning one or simply appreciate learning about different horse breeds, the Cavazaque’s story is one worth celebrating. Embrace the wonder of this remarkable breed and continue to explore the vast and captivating world of horses.
Frequently Asked Questions about Cavazaque
1. What sets the Cavazaque breed apart from other horse breeds?
2. Are there specific health concerns that Cavazaques are prone to?
3. How much exercise and training does a Cavazaque typically require?
4. Are there any unique grooming practices recommended for Cavazaques?

Tech
How Modern Technology Is Revolutionizing Courier Services

Recently, courier services have adapted to cater to the needs of a rapidly changing, tech-savvy society. With technological advancements, customers expect faster, more reliable, and transparent delivery options for their personal and business needs. Modern courier services offer real-time tracking, same-day delivery, and streamlined logistics, ensuring packages arrive safely and efficiently. Whether delivering small parcels or larger shipments, these services cater to local and international markets. For those needing a specialized service, cargo vans delivery service Jacksonville FL, provides an ideal solution for businesses looking to move goods quickly and efficiently within the region.
Real-Time Tracking
One of the most significant changes in the courier industry is the introduction of real-time tracking systems. Customers can now track their packages at every stage of the delivery process, offering peace of mind and increasing transparency. Various tools and apps allow users to see the exact location of their parcel and estimated delivery times.
Real-time tracking benefits the end-users and provides valuable data to courier companies. This information helps optimize routes, manage downtime and improve service reliability. In a competitive market, such features can make or break a business. The importance of real-time tracking is further underscored by consumer demand for transparency and proactive communication throughout the delivery process.
Automated Routing
Automated routing systems utilize sophisticated algorithms to determine the most efficient delivery routes. This minimizes delivery times and reduces fuel consumption, which is crucial for operational efficiency. These systems can adjust real-time routes based on traffic conditions, weather patterns, and other variables.
Implementing automated routing can significantly reduce operational costs. With real-time data analytics, companies can better manage their fleets, adjust to unforeseen circumstances, and ensure timely deliveries. This level of optimization leads to a more sustainable business model. Additionally, automated routing reduces the environmental impact by optimizing fuel usage and lowering emissions, making it a win-win for businesses and the planet.
Same-Day Delivery
With the rise of e-commerce, same-day delivery has become increasingly popular. Companies are investing in technologies and logistics networks that can handle quick turnarounds. While this service was once exclusive to large corporations, advancements have made it accessible to smaller businesses as well.
Same-day delivery serves as a competitive advantage in the crowded e-commerce space. Businesses that offer this service can attract more customers, boost sales, and foster brand loyalty. The ongoing improvements in logistics make it possible to offer same-day delivery to a broader audience. This meets consumer expectations and helps companies differentiate themselves in a market where speed and reliability are paramount.
Enhancing the Customer Experience
Improving customer experience is at the heart of technology adoption in the courier industry. Features like real-time notifications, flexible delivery windows, and easy returns are designed to make the process seamless. Happy customers are likelier to remain loyal and recommend the service to others.
Customer-centric features are not just add-ons but essential components of a successful courier service. Investing in user-friendly technologies can increase customer retention rates and market share. In the customer’s age, experiences matter as much as the products delivered. Today’s consumers prioritize convenience, and companies that deliver a superior experience will stand out in a highly competitive landscape.
Tech
Looksmax AI: Revolutionizing Personal Aesthetics with Advanced Technology

Understanding Looksmax AI
1. Defining Looksmax AI
Looksmax AI refers to a category of artificial intelligence tools and technologies aimed at improving or optimizing individual appearance. The term “looksmax” is derived from internet slang, where “max” signifies the act of maximizing one’s potential in a given area. In this context, it involves leveraging AI to enhance physical features, appearance, and overall aesthetics.
2. Technological Foundations
The core of Looksmax AI lies in its use of advanced machine learning algorithms, computer vision, and data analytics. Here are some of the key technological components:
- Computer Vision: This technology enables AI systems to interpret and analyze visual data. Through computer vision, Looksmax AI can assess various aspects of a person’s appearance, such as facial features, skin quality, and body proportions.
- Machine Learning Algorithms: These algorithms are trained on vast datasets to recognize patterns and make predictions. In Looksmax AI, machine learning helps in recommending personalized beauty routines, skincare regimens, and cosmetic procedures based on individual characteristics.
- Data Analytics: AI systems utilize data analytics to process and analyze information from various sources, including user inputs, social media profiles, and cosmetic industry trends. This helps in tailoring recommendations and solutions to individual needs.
Applications of Looksmax AI
1. Personalized Skincare and Beauty Routines
One of the primary applications of Looksmax AI is in the realm of skincare and beauty. AI-driven platforms can analyze a person’s skin type, texture, and concerns to provide customized skincare routines. For example, an AI tool might recommend specific products, routines, and treatments based on individual skin analysis.
2. Virtual Makeover Tools
Virtual makeover tools powered by Looksmax AI allow users to experiment with different makeup looks and hairstyles in a virtual environment. These tools can simulate the effects of various cosmetics and hairstyles, helping users make informed decisions about their appearance.
3. Aesthetic Enhancement Recommendations
Looksmax AI can offer recommendations for cosmetic procedures and treatments based on a person’s appearance goals. For instance, an AI system might suggest certain types of cosmetic surgery, dermatological treatments, or non-invasive procedures to achieve desired aesthetic outcomes.
4. Fitness and Body Image Optimization
Beyond skincare and cosmetics, Looksmax AI extends to fitness and body image optimization. AI-driven platforms can provide personalized workout plans, dietary recommendations, and body measurements analysis to help individuals achieve their desired physique.
Ethical Considerations
1. Privacy and Data Security
With the rise of Looksmax AI, concerns about privacy and data security have become prominent. AI systems often require access to personal data, including images and biometric information. Ensuring that this data is handled securely and ethically is crucial to maintaining user trust.
2. Body Image and Self-Esteem
The influence of Looksmax AI on body image and self-esteem is a significant ethical concern. While AI tools can provide valuable recommendations, they also have the potential to perpetuate unrealistic beauty standards and contribute to body dissatisfaction. It is essential for developers and users to approach Looksmax AI with a balanced perspective, emphasizing self-acceptance and diversity.
3. Accessibility and Inclusivity
Another ethical consideration is the accessibility and inclusivity of Looksmax AI technologies. Ensuring that these tools are available to individuals from diverse backgrounds and with varying needs is important for promoting equitable access to beauty and wellness solutions.
Future Trends and Developments
1. Integration with Augmented Reality (AR)
The future of Looksmax AI may involve greater integration with augmented reality (AR). AR technology can enhance virtual makeover tools by providing more immersive and interactive experiences. Users could visualize potential changes in real-time and make more informed decisions about their appearance.
2. Advancements in Personalization
As AI technology continues to evolve, the level of personalization in Looksmax AI is expected to increase. Future developments may include more precise recommendations based on individual genetic information, lifestyle factors, and real-time data analysis.
3. Ethical AI Development
The future of Looksmax AI will likely see a stronger emphasis on ethical AI development. Developers and researchers will need to prioritize transparency, user consent, and responsible data usage to address privacy concerns and promote positive body image.
4. Integration with Wearable Technology
Looksmax AI could also integrate with wearable technology, such as smartwatches and fitness trackers, to provide a more comprehensive approach to personal appearance optimization. This integration may offer real-time insights and recommendations based on biometric data.
Conclusion
Looksmax AI represents a fascinating intersection of artificial intelligence and personal aesthetics, offering innovative tools and solutions for enhancing individual appearance. As the technology continues to advance, it is essential to consider the ethical implications and strive for a balanced approach that promotes self-acceptance and inclusivity. By harnessing the potential of Looksmax AI while addressing its challenges, we can look forward to a future where technology and personal beauty harmoniously coexist.
Tech
Tip Screens: Revolutionizing Tipping Practices in the Digital Age

The Emergence of Tip Screens
The introduction of point-of-sale (POS) systems with integrated tipping options has its roots in the rise of cashless transactions. As consumers began using debit and credit cards for even small purchases, businesses sought ways to preserve or even enhance tipping opportunities that had traditionally relied on cash. The result was the development of digital payment platforms like Square, Clover, and Toast, which included built-in tipping functionalities.
Tip screens offer customers a selection of tipping options, usually based on a percentage of the total bill, or sometimes a custom tip option. The percentage options typically range from 10% to 25%, encouraging customers to leave a gratuity even in situations where tipping may not have been the norm, such as at quick-service counters or for takeout orders.
The Psychology of Tip Screens
The psychology behind tip screens and how they influence consumer behavior is fascinating. Researchers have found that the design of these systems can have a significant impact on how much people tip. Pre-set tipping options often anchor the customer’s decision-making process, guiding them toward the higher percentages. For example, if the screen offers 15%, 20%, and 25% as options, many customers feel compelled to choose at least the middle option to avoid seeming “cheap.”
Additionally, the public nature of these screens plays into social norms and pressure. When a customer is handed a tablet or payment device, and the employee is standing nearby, there is an implicit expectation to leave a tip. Many feel awkward skipping the tip or selecting the lowest option, especially if the worker can see their choice. This dynamic can lead to higher tip amounts compared to traditional methods where tipping is done discreetly, like leaving cash on a table.
Benefits for Businesses and Workers
Increased Revenue for Workers
One of the clear advantages of tip screens is the potential for service workers to earn more in tips. By prompting every customer to tip, regardless of the service provided, digital tipping systems have increased the frequency and size of gratuities. This is particularly beneficial in industries where employees rely on tips to supplement their often-low base wages.
Moreover, because the system is automatic, it can reduce the awkwardness of asking for tips, which many workers feel uncomfortable doing. By letting the technology handle the request, employees can focus on providing good service, knowing that a prompt to tip is built into the payment process.
Streamlined Operations for Businesses
From a business perspective, digital tipping has streamlined operations in several ways. First, it simplifies the payment process. There is no longer a need for cash handling or calculating exact change, which speeds up transactions. Additionally, businesses that adopt digital tipping platforms can more easily track tips, ensuring accurate accounting and better transparency.
Furthermore, because the tipping process is automated, businesses can benefit from higher tip averages, which can reduce turnover by keeping employees happier with their income. Many businesses have seen a marked improvement in employee satisfaction as a result of implementing these systems, as workers feel that they are more fairly compensated for their efforts.
Challenges and Criticisms
Customer Backlash
Despite the advantages, tip screens have faced criticism, primarily from customers who feel that they are being pressured into tipping in situations where it was previously optional or unnecessary. For instance, some people are uncomfortable tipping at fast-casual restaurants, coffee shops, or even retail stores where the service is minimal. The placement of the tip prompt in these settings can create a sense of obligation, which can lead to frustration or even resentment.
Moreover, the rise of tip fatigue is a growing concern. As more businesses adopt tip screens, consumers are frequently asked to tip for services they don’t traditionally associate with tipping. This constant barrage of requests can lead to tipping fatigue, where customers begin to feel overwhelmed and less likely to tip generously or at all.
Wage Structure Implications
Another criticism revolves around the wage structure in industries reliant on tipping. Some argue that the increased emphasis on tips through digital systems perpetuates the low-wage model, particularly in sectors like food service. Instead of raising base pay for employees, businesses may continue to rely on tips to compensate workers, which can be inconsistent and dependent on customer generosity.
There is also the issue of fairness in tip distribution. In some establishments, tips are pooled and shared among all employees, from servers to kitchen staff. While this can create a sense of teamwork, it can also lead to disputes about how tips should be divided, particularly when some workers interact more directly with customers than others.
Technological Issues
Finally, there are technological challenges to consider. Tip screens require robust POS systems and reliable internet connections. Any disruption to these systems can delay transactions or prevent tips from being processed altogether. Furthermore, not all customers are comfortable with digital tipping methods, especially older generations who may prefer cash transactions.
The Future of Digital Tipping
The future of tip screens and digital tipping systems is likely to evolve as consumer habits and technology continue to change. One possibility is the further integration of artificial intelligence (AI) and machine learning to optimize the tipping process. For instance, AI could analyze customer behavior and suggest personalized tipping options based on factors like purchase history or frequency of visits. This could create a more tailored experience for consumers while maximizing tips for employees.
Another potential development is the growth of contactless tipping. As contactless payments become more widespread, particularly in the wake of the COVID-19 pandemic, tipping options may evolve to include features like QR codes or mobile app-based tipping. This could provide even more convenience for customers and encourage tipping in situations where it is currently less common.
Additionally, as debates around wage fairness continue, some companies may explore hybrid models that combine higher base wages with optional digital tipping. This could alleviate some of the pressure on customers while ensuring that employees are fairly compensated regardless of tip amounts.
Conclusion
The advent of tip screens represents a significant shift in how gratuities are handled in the service industry. While they offer clear benefits to workers and businesses by increasing tip amounts and streamlining payment processes, they also raise questions about customer pressure, wage fairness, and the future of tipping as a cultural norm.
As digital tipping systems become more prevalent, it is important for businesses to strike a balance between maximizing tips and respecting the preferences of their customers. At the same time, society may need to reconsider the role of tipping in compensating service workers, particularly in industries where low base wages are the norm.
In any case, the rise of tip screens marks a fascinating intersection of technology, psychology, and economics, one that will continue to shape the service industry for years to come. As businesses and consumers alike navigate this evolving landscape, the key will be to ensure that tipping remains a fair and equitable practice for all parties involved.
Tech
Exploring Stars-923: A Comprehensive Insight

Stars-923 is a term that has recently garnered attention in various fields. Whether you’re a tech enthusiast, a gamer, or simply curious about what Stars-923 represents, this article is designed to provide a detailed and in-depth exploration of the subject. By the end of this article, you’ll have a thorough understanding of what Stars-923 is, its applications, and why it has become a topic of interest.
What is Stars-923?
Stars-923 is not a term you’ll find in the mainstream dictionary. It represents a concept, technology, or perhaps a code that is specific to a certain domain. The nature of Stars-923 can vary depending on the context in which it is used. It could be a technological innovation, a unique identifier, or even a niche reference within a specialized community. Regardless of its specific meaning, Stars-923 holds significance in the areas where it is applied.
The Significance of Stars-923
The importance of Stars-923 lies in its application and the value it brings to the table. For some, it might represent a breakthrough in technology, offering new possibilities and solutions. For others, Stars-923 could be a critical component in a system, a game, or an application that they rely on. The versatility of Stars-923 allows it to be relevant in multiple domains, making it a term worth exploring.
Stars-923 in Technology
In the world of technology, Stars-923 might refer to a new algorithm, a piece of software, or a component in a hardware system. It could be a crucial part of a larger system that drives innovation and efficiency. For example, if Stars-923 is a software code, it could be responsible for enhancing the performance of a program or enabling new features that were previously unattainable.
The technological implications of Stars-923 are vast. It might be something that tech developers are incorporating into their projects to push the boundaries of what is possible. The influence of Stars-923 in technology could lead to faster processing speeds, better data management, or more secure systems. Understanding its role in technology is essential for anyone looking to stay ahead in the fast-paced world of tech.
Stars-923 in Gaming
Gamers are always on the lookout for the next big thing, and Stars-923 could very well be it. In the gaming world, Stars-923 might be a code or feature that enhances gameplay, making the experience more immersive and enjoyable. It could be part of a game’s backend system, contributing to the fluidity of the game or enabling advanced graphics and interactions.
For gamers, the presence of Stars-923 in a game could mean the difference between a standard experience and one that is extraordinary. Whether it’s through better graphics, smoother gameplay, or innovative features, Stars-923 could be the key to unlocking a new level of gaming excellence. This makes it a term that gamers and developers alike should pay attention to.
Stars-923 in Everyday Applications
Beyond technology and gaming, Stars-923 might also have practical applications in everyday life. It could be a feature in an app that you use daily, a part of a device you rely on, or even a concept that influences the way certain products are designed. The influence of Stars-923 in everyday applications highlights its versatility and relevance in various aspects of life.
For instance, if Stars-923 is a feature in a smartphone app, it could enhance user experience by providing more intuitive navigation or by improving the app’s functionality. In a broader sense, Stars-923 could be an innovation that makes certain tasks easier, more efficient, or more enjoyable. Understanding its role in everyday applications can help you appreciate the technology and concepts that shape your daily experiences.
The Future of Stars-923
As we look to the future, the potential of Stars-923 continues to grow. It could evolve into something even more significant, influencing a wider range of industries and applications. The future of Stars-923 might involve advancements that are currently unimaginable, pushing the boundaries of what we think is possible.
The ongoing development and integration of Stars-923 into various fields suggest that it will continue to be a topic of interest for years to come. Whether you are a tech enthusiast, a gamer, or someone who enjoys staying informed about the latest trends, keeping an eye on Stars-923 could provide valuable insights into the future of technology and innovation.
Conclusion
Stars-923 is a term that holds significance in various domains. Whether it’s in technology, gaming, or everyday applications, understanding what Stars-923 represents and its potential impact can provide valuable insights into the future of innovation. Keep an eye on this term as it continues to evolve and shape the world around us.
FAQs
What exactly is Stars-923?
Stars-923 is a term that can represent different concepts depending on the context. It might be a technology, a game feature, or an application component.
How is Stars-923 used in technology?
In technology, Stars-923 could refer to a software code, an algorithm, or a hardware component that enhances the performance and functionality of systems.
Is Stars-923 relevant in gaming?
Yes, Stars-923 could be a significant feature in gaming, improving graphics, gameplay, or overall user experience.
Can Stars-923 be found in everyday applications?
Stars-923 might be integrated into everyday applications, enhancing usability, functionality, and efficiency in various devices and software.
What is the future potential of Stars-923?
The future of Stars-923 is promising, with the potential to influence a wide range of industries and continue driving innovation in technology and gaming.
Tech
Optimizing Multi-Cloud Data Storage: Best Practices and Strategies

Table of Contents
- What Is Multi-Cloud Data Storage?
- Benefits of Multi-Cloud Data Storage
- Challenges in Implementing Multi-Cloud Strategies
- Best Practices for Optimizing Multi-Cloud Storage
- Real-World Examples of Successful Multi-Cloud Implementations
- Future of Multi-Cloud Storage
What Is Multi-Cloud Data Storage?
Multi-cloud data storage involves using multiple cloud computing and storage services to manage and store data efficiently. Unlike relying on a single cloud provider, this approach diversifies the storage strategy by incorporating services from various providers. This diversification allows businesses to maximize their data resilience, leverage different cloud providers’ unique features and strengths, and optimize costs.
Benefits of Multi-Cloud Data Storage
- Resilience and Redundancy: Utilizing multiple cloud services mitigates the risk of data loss and reduces downtime, contributing to more stable and reliable systems. When data is spread across various platforms, the impact of a service outage or failure is significantly minimized because other environments are available to take over the workload.
- Cost Efficiency: Multi-cloud strategies allow businesses to manage and optimize costs by selecting the most cost-effective storage options and avoiding vendor lock-in. This allows organizations to adjust their expenses based on their individual requirements and financial limitations, and to easily change providers if more affordable options arise.
- Flexibility and Scalability: Multi-cloud enables dynamic scaling, allowing businesses to quickly adjust their storage needs based on demand. This flexibility ensures enterprises can scale up their storage during peak times and reduce it when demand is lower, optimizing resource utilization and cost.
- Compliance and Security: This strategy helps companies meet different regulatory requirements and improves data security by leveraging the best security practices from various providers. Each provider may offer unique security features, enabling businesses to build a comprehensive and robust security framework.
Challenges in Implementing Multi-Cloud Strategies
Despite its many benefits, implementing a multi-cloud strategy comes with its own set of challenges. For many organizations, a robust multi-cloud strategy ensures their enterprise data storage solutions remain versatile and reliable, even in the face of unexpected challenges. One significant issue is the complex data migration process, which can be time-consuming and costly. Transferring data across various cloud platforms necessitates thorough preparation to maintain data accuracy and reduce disruption. Additionally, multi-cloud environments often involve increased management complications, such as maintaining consistent policies and configurations across all platforms. This complexity can be daunting without the proper tools and expertise.
Security concerns arise in a multi-cloud setup, as each cloud provider may have different security protocols and standards. Ensuring consistent security measures across all platforms is crucial to safeguarding sensitive data. Furthermore, achieving consistent performance across various cloud services can pose difficulties, as infrastructure and service quality variations can affect data accessibility and processing speed. Understanding these challenges is essential to putting practical solutions in place. You can refer to this article from ZDNet for a broader overview of everyday issues.
Best Practices for Optimizing Multi-Cloud Storage
- Centralized Management: Use centralized dashboards or tools to gain visibility and control all cloud environments. These tools integrate the management of various cloud services, simplifying administrative tasks and providing a unified view of system performance and resources.
- Automate Processes: Implement automation for routine tasks such as backups, data transfers, and performance monitoring. Automation reduces the need for manual intervention, minimizes errors, and ensures that critical tasks are performed consistently and efficiently.
- Monitor Performance: Continuously monitor the performance of cloud services to identify and address any issues quickly. Regular performance assessments help maintain optimal operations, prevent potential problems before they escalate, and ensure that service quality meets business needs.
- Prioritize Security: Implement robust security measures across all cloud platforms, including encryption, access control, and regular security audits. To safeguard data from breaches and unauthorized access, it is important to have consistent security policies in place across all environments.
Future of Multi-Cloud Storage
The future of multi-cloud storage is bright, with ongoing advancements aimed at simplifying management and optimization. New technologies such as artificial intelligence (AI) and machine learning (ML) are ready to improve the effectiveness and dependability of multi-cloud setups. For example, AI can predict resource needs and optimize storage allocation, while ML can identify performance bottlenecks and suggest improvements. Furthermore, there are new tools and platforms being created to simplify the incorporation of multi-cloud environments, which helps businesses in adopting and handling this approach more easily. As more organizations recognize the advantages, we expect increased adoption of multi-cloud strategies across various sectors, further driving innovation and improvements in this field.
Tech
The Future of IT Support: Integrating Remote Monitoring Platforms for Excellence

How can Managed Service Providers (MSPs) stay ahead? What tools can they utilize to provide top-notch support and efficiency? Integrating advanced remote monitoring and management (RMM) platforms is the answer. Let us explore the transformative impact of these platforms on MSP operations, highlighting their benefits and future potential.
Streamlining Operations with RMM Platforms
These platforms bring significant efficiency to management and operations. Integrating an RMM for MSPs streamlines processes and enhances service delivery. They ease the burden on IT workers by automating repetitive activities and offering real-time analytics.
MSPs can monitor multiple client environments from a single dashboard, ensuring timely responses to potential issues through:
- Automation of Routine Tasks: Automates updates and patch management.
- Real-Time Monitoring: Offers immediate insights into client systems.
- Centralized Dashboard: Simplifies management across multiple clients.
This streamlining allows MSPs to focus more on strategic initiatives and less on day-to-day troubleshooting, resulting in a more productive and proactive IT support environment.
Enhancing Client Satisfaction
Any MSP’s ability to satisfy its clients is essential to its success. Because these platforms guarantee that systems are always up and operating, they are crucial to sustaining high levels of client satisfaction. With proactive monitoring, issues can be identified and resolved before they impact the client’s business.
RMM platforms also provide detailed reporting, which helps management keep their clients informed about the status and performance of their IT systems. This transparency builds trust and demonstrates the MSP’s value.
Proactive Issue Management
The platform’s unique quality is its capacity to identify problems early on and take action before they get worse. This proactive approach minimizes downtime and prevents minor problems from becoming significant disruptions. MSPs can set up alerts for specific events, ensuring immediate action is taken.
Proactive issue management improves system reliability and reduces the time and cost associated with emergency repairs. This capability allows companies to offer their clients more reliable and cost-effective services.
Future-Proofing IT Support
These platforms are designed to adapt to these changes, offering scalable solutions that grow with the business. This future-proofing ensures that MSPs are always equipped to handle new technologies and increased client demands.
It is groundbreaking that RMM platforms now include machine learning and artificial intelligence. These advanced technologies enhance predictive maintenance and automated problem-solving, setting the stage for even more efficient and reliable IT support.
The Competitive Edge
In a competitive market, MSPs need every advantage to stand out. RMM platforms provide that edge by enabling superior service delivery and operational efficiency. By delivering cutting-edge solutions that satisfy their clients’ changing needs, they aid MSPs in remaining competitive.
By utilizing the power of remote monitoring and management platforms, your management can differentiate themselves from competitors. They can offer faster response times, more reliable services, and higher client satisfaction. This competitive edge is crucial for attracting and retaining clients in a crowded marketplace. The importance of RMM platforms will only increase with the advancement of technology.
The future of IT support is undoubtedly tied to integrating remote monitoring platforms. For MSPs, embracing these tools is essential for staying competitive and delivering exceptional service. With the ability to streamline operations, enhance client satisfaction, manage issues proactively, and future-proof their services, RMM for MSPs is the key to success. Adopting this technology is essential to staying ahead of the curve and not only keeping up.
Tech
How To Keep Up With The Latest Tech

Do you find it hard to keep up with the latest tech trends and developments? You are certainly not alone in this, as tech has been evolving at breakneck speed in recent years, which can make it hard to stay up to date with the best and latest technologies. Whether you are a tech professional looking to keep up with the latest developments or simply curious about new technology, you should know that there are a few ways that you can keep up with the latest trends and developments. This post will look at the best methods that will help you stay current.
Tech Blogs
One of the quickest and easiest ways to keep up with the latest tech news is to read blogs. Many excellent tech blogs post tech news, interviews, tips, tutorials, and other useful content. Checking these blogs on a regular basis will help you stay abreast of all the latest developments.
Tech Podcasts
Similarly, tech podcasts are a fantastic way to learn about the latest technology. Many popular tech podcasts out there cover all you need to know about the world of tech and often include interviews with key industry figures. Podcasts are great because you can listen to them on the go and while completing other tasks, such as cleaning, driving, or exercising.
Learning Centers
Online learning centers are a great way for those looking to learn about tech and develop their skills. Places like the Kong Learning Centre can provide foundational guides that cover key industry concepts and technologies, which is ideal for developers and other tech professionals looking to sharpen their abilities. Learning how to harness tech can be challenging, so learning centers are ideal for those looking to not just learn about tech but also how to use it yourself.
Social Media
Of course, social media can be an excellent platform for learning about the latest news and developments in the tech world. The key is to follow leading industry organizations and individuals so that your feed will be filled with engaging content that will keep you up to date.
Events
Another way to keep up with the latest tech news is to attend industry events. There are always tech events that will showcase different technologies and give you the chance to learn from industry innovators. Of course, many events take place online these days, allowing people to attend no matter where they are located in the world. These events can also be a good opportunity to grow your network.
Online Communities
Engaging in online communities allows you to speak with other tech enthusiasts from all around the world. This can be a great way to discuss new technologies, ask questions, and feel like part of a large global community.
These are a few of the best ways to keep up with the latest tech trends and developments. Whether you work in tech or you simply have an interest in the latest technologies, these methods will help you stay ahead of the curve and get to grips with the best and latest technologies.
Tech
Best Practices for Electrical Safety in Commercial Buildings
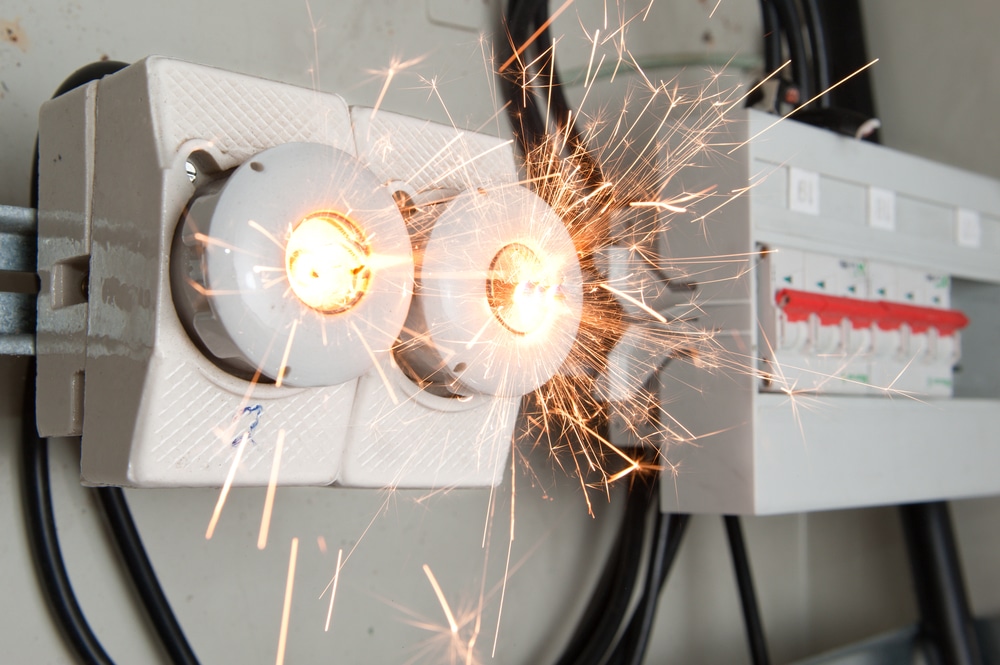
Key Takeaways:
- Understand the importance of electrical safety in commercial environments.
- Learn the essential safety measures to implement in commercial buildings.
- Discover the significance of regular electrical inspections and maintenance.
- Explore the role of employee training in maintaining a safe electrical system.
The Importance of Electrical Safety in Commercial Buildings
Electrical safety is critical to maintaining a secure and functional commercial environment. Neglecting safety measures can result in severe consequences, including electrical fires, equipment damage, and even human injury. According to the National Fire Protection Association (NFPA), an estimated 15% of fires in commercial properties are caused by electrical failures or malfunctions. Such incidents risk human lives and result in significant financial losses and disruptions to business operations. Therefore, businesses must prioritize electrical safety protocols to safeguard their premises and personnel.
To achieve this goal, many companies seek the expertise of professionals, such as a land development engineer, who can provide comprehensive assessments and recommendations. These experts are adept at identifying potential risks and offering solutions that enhance electrical safety in commercial settings.
Regular Electrical Inspections and Maintenance
Regular inspections and maintenance are key to sustaining electrical safety in commercial buildings. It’s advisable to schedule periodic inspections by qualified professionals who can detect and correct any flaws in the electrical system. These experts are trained to identify issues that may not be immediately apparent, such as wear and tear on wiring, corrosion, or other forms of degradation. Additionally, maintaining a record of all inspections and repairs can help track the condition of electrical components and plan future maintenance effectively. By being proactive, little problems can be stopped before they become bigger ones, protecting the electrical system’s dependability and safety.
Scheduling Periodic Inspections
Depending on the complexity and age of the electrical system, inspections should be done at least once a year, if not more often. These inspections should include testing safety equipment like smoke detectors and alarms, assessing circuit load capacities and checking wiring integrity. Frequent inspections reduce the chance of electrical fires and equipment failures by assisting in the early detection of possible problems.
Maintaining Inspection Records
Keeping detailed records of inspections and repairs can be invaluable. These records help assess the electrical system’s health over time and provide crucial information for planning timely maintenance or upgrades. Additionally, documentation can be useful for complying with safety regulations and standards, ensuring that the business meets all requirements for electrical safety.
Addressing Common Electrical Issues
Common electrical issues in commercial buildings include overloaded circuits, exposed wiring, and outdated equipment. Addressing these issues promptly is vital to prevent disruptions and hazards. Overloaded circuits can lead to frequent tripping of breakers, and exposed wiring poses a danger of electric shock or fire. For instance, replacing old wiring and upgrading to energy-efficient lighting and appliances can significantly reduce the risk of electrical malfunctions and improve overall safety. By proactively addressing these common issues, businesses can maintain a safer and more efficient electrical system.
Overloaded Circuits
An overloaded circuit can cause breakers to trip frequently and lead to overheating, which poses a significant fire hazard. Businesses should ensure that circuits are appropriately rated for their load and avoid plugging too many devices into one outlet. Regular assessments of circuit loads and adjustments as needed can prevent overloads and enhance safety.
Exposed Wiring
Exposed wiring is dangerous as it can easily contact people or flammable materials. Regular inspections should include checks for exposed or damaged wires and repairing them promptly. Electrical accident risk can be considerably decreased by ensuring all wiring is adequately insulated and shielded.
Leveraging Technology for Electrical Safety
Technology is crucial in enhancing electrical safety. Modern advancements, such as smart electrical panels and monitoring systems, allow for real-time tracking of electrical usage and early detection of anomalies. Leveraging these technologies can help businesses avoid potential issues and maintain a safer electrical system. Embracing technological solutions can lead to more efficient management and a greater understanding of electrical systems.
Smart Electrical Panels
Bright panels offer real-time monitoring and control over electrical systems, allowing facility managers to detect irregularities and optimize power distribution efficiently. These panels can provide alerts and notifications when potential issues arise, enabling prompt action to prevent problems from escalating.
Monitoring Systems
Modern monitoring systems can notify staff members of possible issues before they become more serious, allowing for prompt action and lowering the possibility of mishaps or equipment failure. Monitoring systems can measure temperature, current flow, voltage levels, and other factors to provide a comprehensive picture of the electrical system’s state.
Creating an Electrical Safety Culture
Creating a culture of electrical safety within the workplace involves continuous education and vigilance. Encouraging employees to report electrical issues immediately and conducting regular safety drills can reinforce the importance of electrical safety. A proactive approach ensures that safety remains a top priority and minimizes the risk of accidents. Fostering a safety-first mindset among employees can lead to a more compliant and aware workforce.
Encouraging Reporting
Encouraging workers to report electrical problems in a comfortable environment can expedite the treatment of minor issues and keep bigger hazards at bay. Employees can efficiently voice issues by implementing a reporting system that is easy to understand and accessible.
Regular Safety Drills
Regular safety drills ensure that all employees are prepared to respond appropriately in an electrical emergency, enhancing workplace safety. Drills should be designed to simulate real-life scenarios and provide practical experience in handling emergencies.
Conclusion
Upholding electrical safety in business buildings is a continuous duty that calls for attention to detail and preemptive action. Businesses may dramatically lower the risk of electrical dangers by making frequent inspections a priority, putting in place crucial safety procedures, and providing employee training.
Tech
Powering Your Business into the Future: How to Seamlessly Transition to Commercial Solar Energy

As the globe becomes increasingly conscious of environmental sustainability and the economic pressures of operating a business, companies are looking for ways to cut costs and reduce their carbon footprint. One viable solution that is gaining traction is the transition to solar power. In this pursuit, understanding the multitude of benefits and considerations is critical for business leaders who are interested in making an informed decision. The focus of this article is to guide your business through the seamless adoption of solar panels for business, the economic gains, and the crucial role a consultancy firm like Johnson Energy Consulting can play in this process.
Understanding the Economic Advantages
Investing in solar energy is not just a nod to environmental stewardship; it’s a strategic financial decision as well. Solar panels can provide a substantial reduction in electricity bills, delivering real savings that can be channelled back into growing your business. Furthermore, there are often government incentives and rebates available which serve to lower the initial setup cost of solar installations.
Yet, understanding the complex landscape of suppliers, technology options, and financial models can prove daunting. That’s where obtaining comprehensive commercial solar quotes plays an integral role. Accurate quotes not only deliver clarity on upfront costs but also provide forecasts on long-term savings and return on investment timelines.
Environmental Commitment as a Business Ethos
Today’s consumers and business partners are increasingly favouring companies with a strong commitment to sustainability. By transitioning to commercial solar energy, businesses send a powerful message that they prioritise global citizenship. Reduced greenhouse gas emissions and lessened dependence on fossil fuels are significant outcomes of this switch, aligning business practices with ecological responsibility.
Assessing Solar Suitability for Your Business
To efficiently transition to solar power, first, your business facilities must be evaluated for solar viability. Key factors to consider include the geographical location, roof integrity, and the orientation, which directly influence the efficiency of the solar panels. Such assessments can sometimes require a high degree of technical expertise.
Navigating Technical Complexities
When considering solar energy, the technical intricacies can seem overwhelming. Different solar panel brands and types offer varying degrees of efficiency, longevity, and warranty conditions. Moreover, the integration of solar power with existing electrical systems can pose additional challenges. This technical minefield underlines the importance of expert consultation to avoid common pitfalls and ensure a system that is tailor-made for your business needs.
Why Choose Johnson Energy Consulting?
To navigate these complexities, partnering with a reputable consultancy such as Johnson Energy Consulting can significantly streamline the process. A consultancy can provide a wealth of industry knowledge, access to trusted suppliers, and manage the entire project – from the initial quotes and assessments through to implementation.
The Role of Consultants in Solar Transition
Consultancy firms specialise in understanding your business requirements, energy usage patterns, and financial objectives to deliver a bespoke solar solution. They work to secure competitive commercial solar quotes, facilitate necessary approvals, and can monitor installation quality and effectiveness post-implementation. This holistic approach ensures not only a transition to solar power but also that your investment yields the expected financial and environmental benefits.
Maximising Your Solar Investment
While the transition to solar can be filled with opportunities, maximisation of your solar investment is key. This requires a strategic approach to sizing your solar system, negotiating purchase or lease agreements, and understanding the intricacies of solar output in relation to your business operations.
A consultancy can also help set up monitoring systems to track solar energy production, usage, and performance over time. These systems ensure your solar panels are performing optimally and help identify any areas that may require maintenance or upgrades.
Long-Term Business Growth and Sustainability
Adopting solar power is not just a move towards sustainability but signifies a commitment to long-term business growth. As energy prices continue to rise, the savings provided by solar energy can become a significant competitive advantage. Moreover, by showcasing a dedication to green initiatives, businesses can enhance their brand reputation and customer loyalty.
In an era where every business decision counts, the integration of solar technology presents an avenue for cost savings, operational efficiency, and environmental responsibility. Obtaining the right solar panels for business is more than an investment in energy; it’s an investment in the future vitality and public image of your company.
Preparing for the Future
As we look forward, renewable energy sources like solar power are slated to become even more integral to business operations. Understanding the full spectrum of benefits and considerations of transitioning to commercial solar power is imperative for future-proofing your business.
Conclusion
The journey to roll out commercial solar energy can be complex, but it doesn’t have to be cumbersome. With the right partner and a comprehensive plan in place, your business can effortlessly make the switch. Embracing solar power with the guidance of seasoned experts like Johnson Energy Consulting will energise your business today and sustain it for decades to come.
Seize the opportunity for growth, resilience, and a greener future by integrating solar energy into your business model. Power your business into the future; begin your journey to clean, sustainable, and cost-effective energy today.
Tech
Top 3 Cross Browser Testing Tools You Should Know

Cross Browser Testingis important when it comes to designing applications for browsers so that the page looks good on all the different devices. Given the number of browsers and versions available, it is simply impractical to go through the process of manually testing a web application across the various combinations. Cross browser testing tools are used at this point. They enable the testing process to be tested across different browsers, which is a very convenient feature that saves a lot of time. Here are the top 3 cross browser testing tools you should consider.
1. Testsigma
Testsigma is a leading intelligent test automation platform with integrated cross-browser testing capabilities. It allows users to write test scripts in simple English, which can run on multiple browsers and devices without modifications. Key features include browser-agnostic scripts that reduce maintenance, a real device cloud with 3000+ options, self-healing scripts that adapt to application changes, and comprehensive reporting for easy failure tracing.
Testsigma’s integration features enable continuous testing across browsers, supporting frequent testing and high-quality web application releases. This platform empowers teams to shift testing left in the development process, enhancing overall software quality and efficiency. Testsigma’s user-friendly approach and advanced capabilities make it a top choice for organizations seeking to streamline their cross-browser testing processes and improve their web application development workflow.
2. Testim
Testim is an automated testing tool for web and mobile applications, offering high-speed cross-browser testing. Its integrated recorder simplifies test script creation without coding. Key features include parallel execution across multiple browsers and devices for rapid results, advanced root cause analysis for quick debugging, robust connectors for integration with CI/CD tools DevOps, and an automated bug tracker that logs issues with screenshots and step-by-step guides.
Testim accelerates test cycles through parallel testing and intelligent test generation based on past executions. This approach enables organizations to shift testing left in the development process, facilitating faster delivery of reliable web applications. Testim’s combination of user-friendly features and advanced capabilities makes it an efficient solution for teams looking to streamline their testing processes and improve overall software quality.
3. Ranorex Studio
Ranorex Studio is a leading GUI and cross-browser testing tool suitable for enterprise-level application testing on desktop and mobile browsers. It offers a click-and-record feature for creating test automation scripts without coding. Key features include broad browser coverage for testing on current and past versions of desktop and mobile browsers, dynamic recognition of test objects even after application changes, comprehensive reporting with detailed failure information, and workflow integration with CI/CD tools.
Ranorex Studio’s integration capabilities enable sequential and continuous cross-browser testing, allowing teams to run tests across multiple browsers early in the development cycle for quick results. This comprehensive approach to testing, combined with its user-friendly interface and robust features, makes Ranorex Studio an effective solution for organizations seeking to enhance their cross-browser testing processes and improve overall software quality.
Conclusion
Ensuring that web testing is done across browsers frequently is an essential feature in creating optimal user experiences. The automated cross browser testing such as Testsigma, Testim and Ranorex studio enable the left shifting of testing, testing across browsers at an early stage and releasing high quality web applications in the market. All of these tools support cross browser testing, but with Testsigma coming out slightly ahead due to its no code, auto healing and easy to use platform.
-

 Health7 months ago
Health7 months agoGorgeous – Definition, Meaning & Synonyms
-

 News7 months ago
News7 months agoIs Ofleaked.net Legit or Scam?
-

 Tech7 months ago
Tech7 months agoGreenbits: Revolutionizing Sustainable Agriculture
-

 Life Style7 months ago
Life Style7 months agoA Comprehensive Guide to OpenHousePerth.net Insurance
-

 Tech7 months ago
Tech7 months agoGEEKZILLA.TECH HONOR MAGIC 5 PRO REVIEW
-

 Tech7 months ago
Tech7 months agoUnderstanding the 2023-1954
-
![[noblocc] Kicked for Being AFK](https://bicimag.com/wp-content/uploads/2024/03/Noblocc-Kicked-for-Being-AFK-1-400x240.webp)
![[noblocc] Kicked for Being AFK](https://bicimag.com/wp-content/uploads/2024/03/Noblocc-Kicked-for-Being-AFK-1-80x80.webp) News7 months ago
News7 months ago[noblocc] Kicked for Being AFK
-

 Business7 months ago
Business7 months agoUncovering кинокрадко: The Dark Side of Film Piracy